overleaf template galleryLaTeX templates and examples — Recent
Discover LaTeX templates and examples to help with everything from writing a journal article to using a specific LaTeX package.

Universidade Federal da Paraíba: Modelo de Patente no Instituto Nacional da Propriedade Industrial (INPI), Brasil conforme versão disponibilizada em Junho de 2020 (ModelodopedidodepatentePI29062020).

A homework template for UConn's CSE-3500 Algorithms & Complexity course.

Otimização do Sequenciamento da Produção em uma Linha de Placas Eletrônicas com Tempos de Setup Dependentes da Sequência

Based on the official MS Word template, with a few stylistic changes.

The purpose of the class yathesis is to facilitate dissertations’ typesetting of theses prepared in France, whatever disciplines and institutes. It implements most notably recommendations from the Ministry of Higher Education and Research and this, transparently to the user. It has also been designed to (optionally) take advantage of powerful tools available in LaTeX, including packages: biblatex for the bibliography ; glossaries for the glossary, list of acronyms and symbols list. The yathesis class, based on the book class, aims to be both simple to use and, to some extent, (easily) customizable.

Sample Ph.D. dissertation to meet University at Albany requirements as of 2020
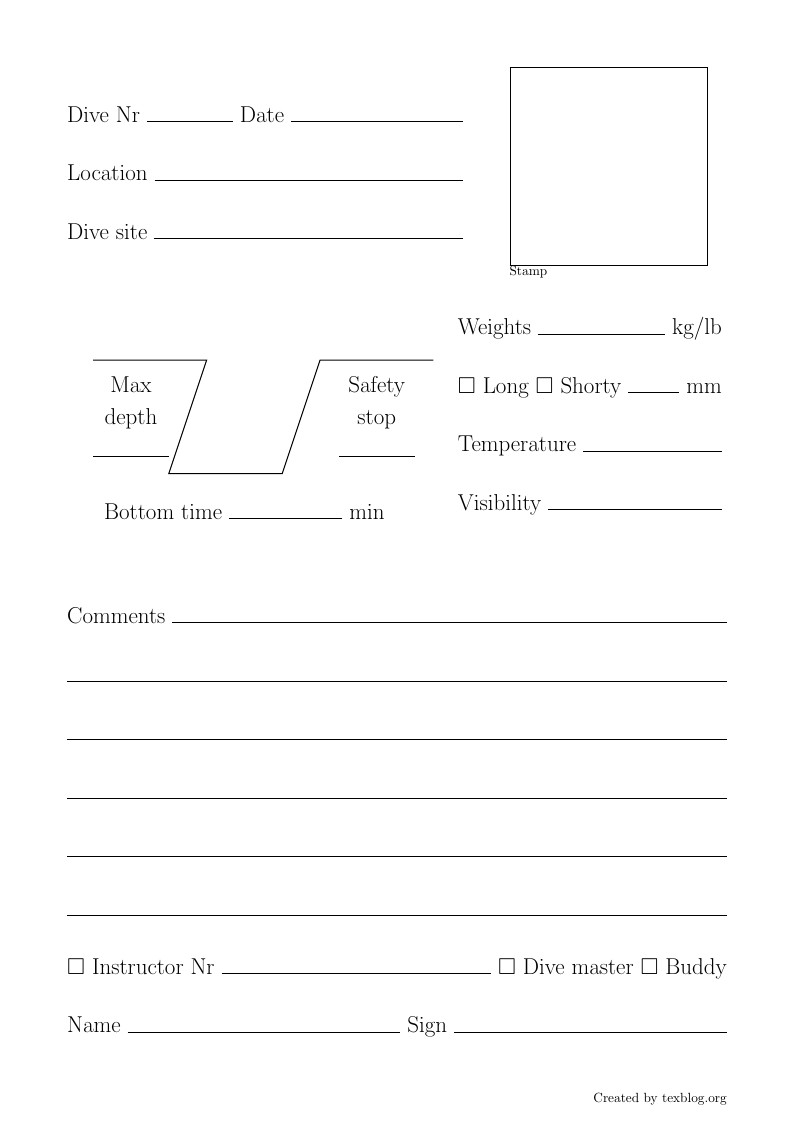
This template contains all information I would personally log after a dive. Feel free to use and /or modify it to create your own custom dive log book. If you are not familiar with LaTeX and would like to make minor changes, drop me a comment on my blog at http://texblog.org/2015/07/22/diy-scuba-diving-log-book/

This is the official template for papers to be submitted to Open Geomechanics.
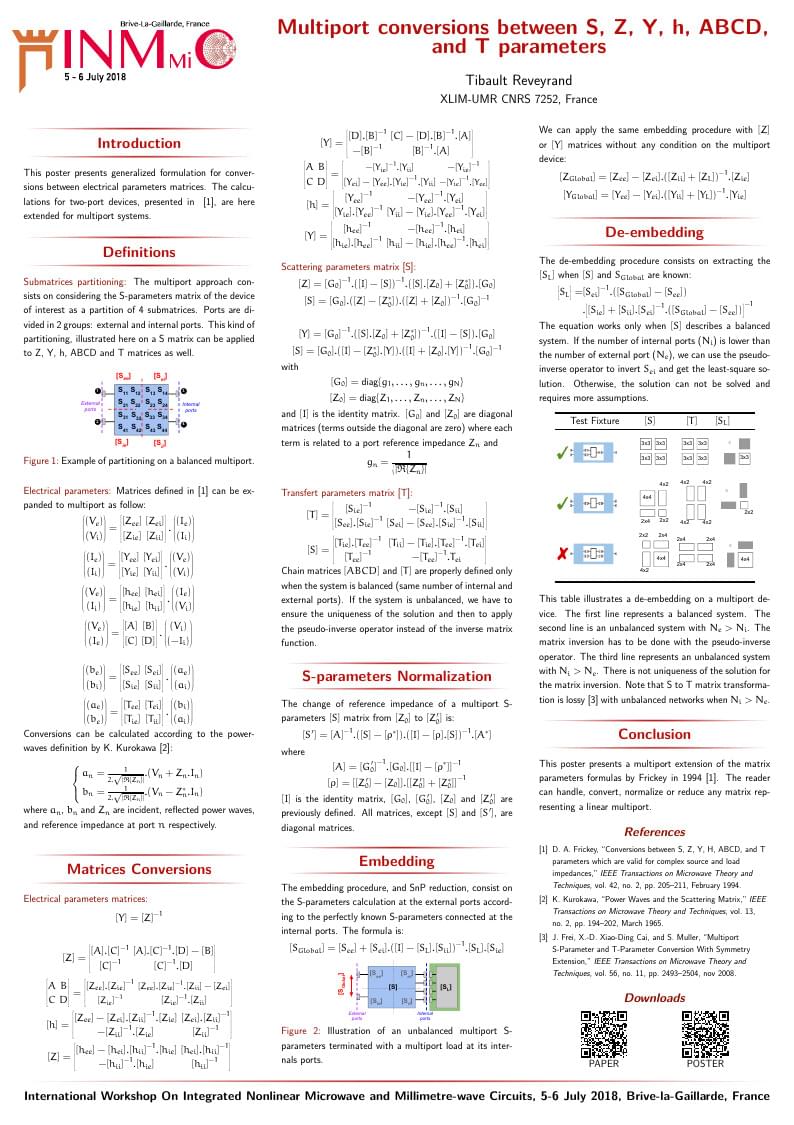
«Multiport conversions between S, Z, Y, h, ABCD, and T parameters.» Integrated Nonlinear Microwave and Millimetre-wave Circuits (INMMIC 2018), Brive-la-gaillarde, France, July 2018. Article: http://www.microwave.fr/publications/151.pdf Poster: http://www.microwave.fr/publications/151p.pdf
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.